Portable TrueCrypt – A software designed to protect your important data by encrypting it

TrueCrypt is a software designed to protect your important data by encrypting it. It can also maintain an on-the-fly-encrypted volume (data storage device).
Files can be copied to and from a mounted TrueCrypt volume just like they are copied to/from any normal disk (for example, by simple drag-and-drop operations). Files are automatically being decrypted on-the-fly (in memory/RAM) while they are being read or copied from an encrypted TrueCrypt volume.
Similarly, files that are being written or copied to the TrueCrypt volume are automatically being encrypted on-the-fly (right before they are written to the disk) in RAM. Note that this does not mean that the whole file that is to be encrypted/decrypted must be stored in RAM before it can be encrypted/decrypted. There are no extra memory (RAM) requirements for TrueCrypt.
Here are some key features of “Portable TrueCrypt”:
· Creates a virtual encrypted disk within a file and mounts it as a real disk.
· Encrypts an entire partition or storage device such as USB flash drive or hard drive.
· Encrypts a partition or drive where Windows is installed (pre-boot authentication).
· Encryption is automatic, real-time (on-the-fly) and transparent.
Provides two levels of plausible deniability, in case an adversary forces you to reveal the password:
· 1) Hidden volume (steganography ? more information may be found here).
· 2) No TrueCrypt volume can be identified (volumes cannot be distinguished from random data).
· Encryption algorithms: AES-256, Serpent, and Twofish. Mode of operation: XTS




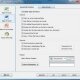
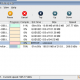


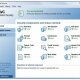

[…] Mã hóa và bảo vệ dữ liệu với TrueCrypt (download tại đây) Một trong những cách an toàn nhất để giữ bí mật cho các dữ liệu quan […]
[…] 9- Mã hóa và bảo vệ dữ liệu với TrueCrypt (download tại đây) […]
[…] 9- Mã hóa và bảo vệ dữ liệu với TrueCrypt (download tại đây) […]
[…] 9- Mã hóa và bảo vệ dữ liệu với TrueCrypt (download tại đây) […]
[…] 9- Mã hóa và bảo vệ dữ liệu với TrueCrypt (download tại đây) […]
[…] 9- Mã hóa và bảo vệ dữ liệu với TrueCrypt (download tại đây) […]
[…] trước đây. 9- Mã hóa và bảo vệ dữ liệu với TrueCrypt (download tại đây) Một trong những cách an toàn nhất để giữ bí mật cho các dữ liệu quan […]